Blocking credential stuffing bots is a game of whack-a-mole. And HUMAN Bot Defender is the best in the game. But when Bot Defender is partnered with Credential Intelligence, it changes the game altogether. Let me explain.
A lot of people reuse passwords across multiple online accounts (65% according to a Google survey). This means that if an attacker steals credentials via a breach on site A, they can likely use that information to unlock accounts on Site B. And if you’re Site B, you have no oversight to prevent the breach on Site A — even though your business could suffer an attack as a result.
While it would take forever to manually test combinations of credentials across multiple sites, it becomes quite easy with credential stuffing bots. So, that’s exactly the method that attackers use. The Verizon 2023 Data Breach Investigations Report found that stolen or compromised credentials are at the root of just under 50% of all breaches.
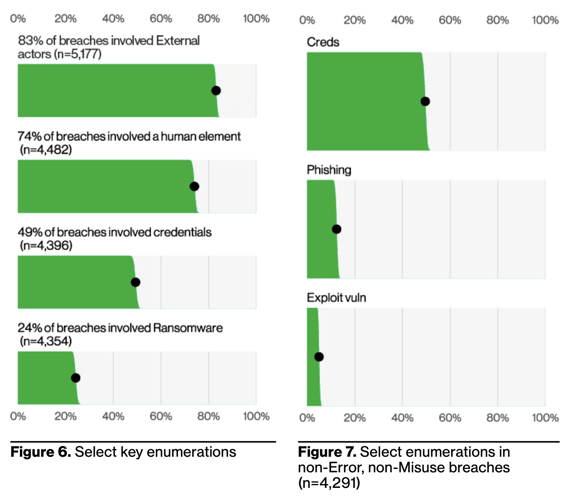
Stopping credential stuffing and account takeover attacks requires layered defenses
Credential stuffing attacks are increasingly sophisticated and simple to execute. Due to the rise of crime-as-a-service (CAAS), even amateurs can obtain the tools and knowledge needed to execute cybercrime. Stolen credentials are easy to get and they’re continuously reusable against a variety of sites. Once fraudsters get their hands on valid credentials, they can take over accounts and commit all types of fraud. This includes making fraudulent purchases, transferring funds, emptying gift cards and opening new credit applications, to name a few examples.
Traditionally, there have been two best practice solutions to mitigate credential stuffing:
- Switch to a more robust authentication mechanism such as multi-factor authentication (MFA), which isn’t a viable solution for many websites because of the friction and cost it introduces. Furthermore, savvy cybercriminals are able to beat MFA by exploiting vulnerable extensions or using techniques such as prompt bombing.
- Adopt security measures to block attacks as they happen, which does not deter future attacks. Even when login attempts are blocked, the targeted site has no record of the credentials the attacker used, and no way to force password resets.
Even if a breach is mitigated at the source, the compromised credentials are likely still applicable elsewhere. In order to end the cycle, digital businesses must nip unauthorized logins in the bud, aka the compromised credentials themselves. Blocking bots is critical and necessary, but accounts are still vulnerable to takeover as long as the credentials are compromised.
Credential Intelligence delivers actionable visibility
Every day, HUMAN witnesses credential stuffing attack attempts levied against the largest websites in the world. We see more than 20 trillion digital interactions every month, which gives us unique visibility into what attacks are happening each day. We are able to see which credentials are being used in real-world attacks, in real time — and we can share that intelligence.
Credential Intelligence passes our visibility to our customers. The solution leverages a proprietary database of compromised credentials curated from continuous monitoring of dark web sources and attacks happening “in the wild.” When a login is attempted using a compromised credential pair, Credential Intelligence automatically signals in real time that the account is compromised and notifies the customer to force a password reset. This reduces the number of accounts that are vulnerable to takeover in the first place.
Traditional credential monitoring tools often rely on static and outdated lists of known compromised credentials. Researchers found more than 24 billion stolen credentials for sale on the dark web in 2022, and that number is likely growing. With so many credentials to choose from, cybercriminals are likely to avoid using credentials on known monitoring lists in favor of unknown or zero-day compromised credentials. Static lists can’t keep up with real-time breaches enough to offer meaningful and complete information. Businesses need a solution that monitors real-world attacks as they happen and flags the credentials that attackers are using now, instead of what might have been compromised and used in the past.
Bot Defender and Credential Intelligence throw a one-two punch
By removing your vulnerable surface area, Credential Intelligence makes credential stuffing attacks economically inviable. It turns a previously renewable resource — compromised credentials — into a single-use resource. This happens because once a credential pair is seen in a single attack, it will be mitigated across the entire HUMAN network. The result is a long-term decline in credential stuffing attacks and account takeovers (just ask this e-commerce retailer if you don’t believe me).
Bot Defender is an immediate and necessary solution against active credential stuffing attacks. Credential Intelligence is a strategic solution geared towards eliminating future credential stuffing attempts. Together, they form a layered account takeover defense that stops fraud before it happens.