There’s an expression in gambling: “the house always wins.” It refers to how every casino game is built with odds that tilt toward the casino itself. The odds of hitting the jackpot on a slot machine can be as low as one in 34 million. Gambling is, by definition, taking a monetary risk and hoping for a payout.
Sometimes, though, the house and the gamblers aren’t the only ones eyeing the money on the table (just ask the casts of Oceans 11, 12, 13, and 8). The advent of online sports betting has dramatically expanded access to gambling, taking it from the casinos and putting it in the smartphones and laptops we all rely on. But stop me if you’ve heard this before: with new markets and new money flowing through a system comes new opportunities for fraud.
HUMAN’s Satori Threat Intelligence and Research Team recently observed a coordinated account takeover attack on betting platforms. The attack—which was on one platform stymied by HUMAN Bot Defender and Credential Intelligence products—was organized and carried out by a loosely-connected group of hackers and opportunists led by a single threat actor. We’ve dubbed this attack Capra as a "faux-mage" (like an homage, but fake) to the threat actor’s store, on which they openly sell access to hacked accounts.
Account takeover attacks are an existential threat to platforms on which users have account balances, sensitive or personal information, or the ability to share a message with a group of friends or followers. We wanted to explore the anatomy of such an attack and offer an inside look at how account takeover happens and how HUMAN prevents it.
Inside Capra
Pre-attack
Any attack begins with preparation and understanding of the target. Think of a robber “casing the joint” to ascertain the best entry point and the best way to break through the defenses.
In the case of Capra, the threat actor took a list of email addresses from a separate, unrelated data breach and checked those addresses for accounts on the target betting platforms. The threat actor used the target’s page-response to test whether an email address was Registered or Non-Registered. Any email addresses that came back as Non-Registered were removed from the list.
Checking whether an email address has an associated account on a betting platform
Source: Satori Threat Intelligence and Research Team
Following a successful “does this email address have an account” check, the attacker then fires off a request to the betting platform’s authentication server. The request spoofs the OS from which the request originated: rather than whatever OS is in use on the actual account holder’s device, the request presents itself as coming from an OS most commonly used by other servers. The attacker does this because the security checks for requests from this particular OS are less rigorous than those coming from other OSes.
Spoofing the user-agent to bypass security measures
Source: Satori Threat Intelligence and Research Team
The authentication server offers instructions on what steps are required to complete a login. One of those steps is a CAPTCHA, which the attack is able to easily defeat:
Solving the CAPTCHA
Source: Satori Threat Intelligence and Research Team
Solving the CAPTCHA generates an allowlist token, which the attacker captures and uses across the remainder of the attack.
Next, the attacker matches the spoofed OS information from earlier, incorporates the allowlist token provided by the CAPTCHA solve, spoofs information about the version of the platform’s app, and connects with the app’s API endpoint to try to log in.
Notice in the screenshot below the “random string” - this is a mechanism intended to break through a rate-limiting security measure on the API. This helps the attack scale, allowing the threat actor’s followers to maximize their fraud.
RandomString circumventing a time-limit measure on the API login
Source: Satori Threat Intelligence and Research Team
If the threat actor’s login attempt is successful on the API endpoint, they take the credential information to the web endpoint, knowing that the login will work.
Attack
At HUMAN, we’ve often described fraud schemes like Capra as being a race against time; there’s only so long an operation can succeed before it’s discovered and blocked. The threat actor knew this, too, and communicated to their followers that the attack was ready and that anybody wanting to take advantage of the situation should do so quickly “while method works”.
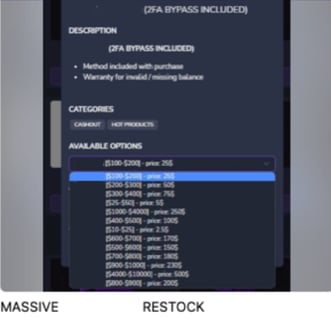
Threat actor selling cracked betting platform accounts expecting a short-lived attack
Source: Satori Threat Intelligence and Research Team
The ringleader sells account information to their followers and offers tips on how to circumvent any two-factor authentication steps a user may have in place.
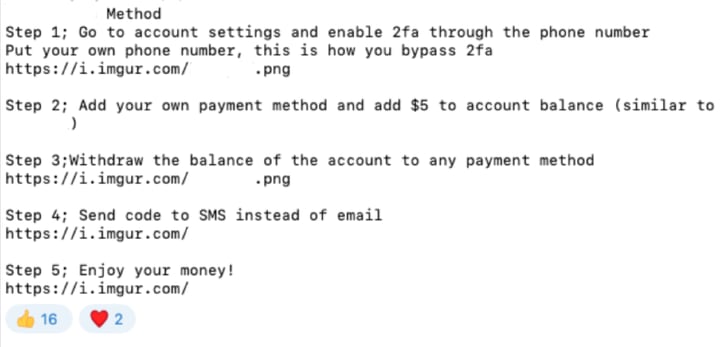
Threat actor coaching followers on how to defeat 2FA protections
Source: Satori Threat Intelligence and Research Team
All of the dominos have been set up; what was needed now was simply for someone to knock the first one over. The attack is on.
Once an attacker is logged into an account, they’re able to check the balance info for the account, change the connected bank information, and drain the account.
Checking balances on cracked accounts
Source: Satori Threat Intelligence and Research Team
Within only a few days of the attack, the ringleader had facilitated the siphoning of thousands of user accounts, with followers openly bragging about how much money they’d stolen:
Screenshots of cashouts shared on private channels by followers of the threat actor
Source: Satori Threat Intelligence and Research Team
Post-Attack
The attack didn’t last very long; it took the platform only a few hours to recognize there was a serious problem, uncover the source, and plug the gaps in the security system. But the damage was done. Thousands of user accounts had been drained and the betting platform had to make them whole.
What’s worse for the victimized platform, however, is the secondary impact of a high-profile attack like Capra. Yes, users are (understandably) angry and yes, the platform has to compensate them for the lost account balances. But the court of public opinion has a long memory, as does the market.
Victimized platforms of ATO attacks may take a hit on a stock market, or may remain in the headlines for months after the fact. Even after a problem is fixed, its impacts will linger.
The ringleader behind Capra had their communication platform shut down shortly after the attack concluded, but a new one cropped up within a matter of hours and had amassed a following of more than 22,000 participants within a few weeks. That platform has also since been dismantled.
Stopping ATOs Before They Happen
One major betting platform was fully protected from Capra by HUMAN Bot Defender and Credential Intelligence:
Snapshots of HUMAN Bot Defender and Credential Intelligence activity during the attack
Source: HUMAN
During the attack, Bot Defender blocked 49 million login attempts to the platform, making up nearly 13% of all login activity during the attack’s time period. Bot Defender by itself protected the vast majority of the platform’s users during the attack.
Some craftier attempts by the threat actor’s gang were blocked by HUMAN Credential Intelligence. 2.4 million login attempts using compromised credentials were caught by Credential Intelligence. As the betting platform had configured Credential Intelligence to force users to reset their credentials following a login attempt using compromised credentials, these users were also fully protected from the attack.
This is the power of the Human Defense Platform; global visibility makes Credential Intelligence and Bot Defender that much more capable of protecting platforms and their users from the impacts of an account takeover.
Recommendations for ATO Prevention
Platform Owners
Platform owners that may be a target for attacks like Capra should consider:
- using tools like HUMAN Bot Defender, Credential Intelligence, and Account Defender for ongoing monitoring of suspicious activity to proactively protect customer accounts
- offer 2FA options via authentication apps, rather than strictly through text/SMS
Users
Users who want to avoid being individually victimized by an ATO attack should consider:
- using a password manager that creates unique passwords for all accounts
- opting into 2FA protections whenever possible
- choosing a pass “phrase,” which may be easier to remember but harder for an attacker to brute force
Final Thoughts
HUMAN Bot Defender, Credential Intelligence, and Account Defender deliver defense-in-depth to stop ATOs from every angle. The combined solution - available as Account Takeover Defense - provides multilayered protection for our customers. While HUMAN’s Satori Threat Intelligence and Research Team continues to hunt for burgeoning attacks, platform managers need to ensure their defenses are up-to-date in order to prevent breaches like Capra.