Many organizations that accept payment cards, either in-person or online, are required to meet a specific set of security standards to protect that sensitive information. These standards—named Payment Card Industry Data Security Standard, or PCI-DSS—are updated periodically to reflect new technologies and new understandings of data security.
The most recent version of the standard, Version 4.0, was introduced in March 2022. For the moment, two different versions are “active:” the aforementioned v4.0 and its predecessor, v3.2.1, with the older standard scheduled to phase out by the end of March 2024. With that timeline in mind, credit card companies and vendors who conduct credit card transactions have until March 2025 to demonstrate compliance with v4.0.
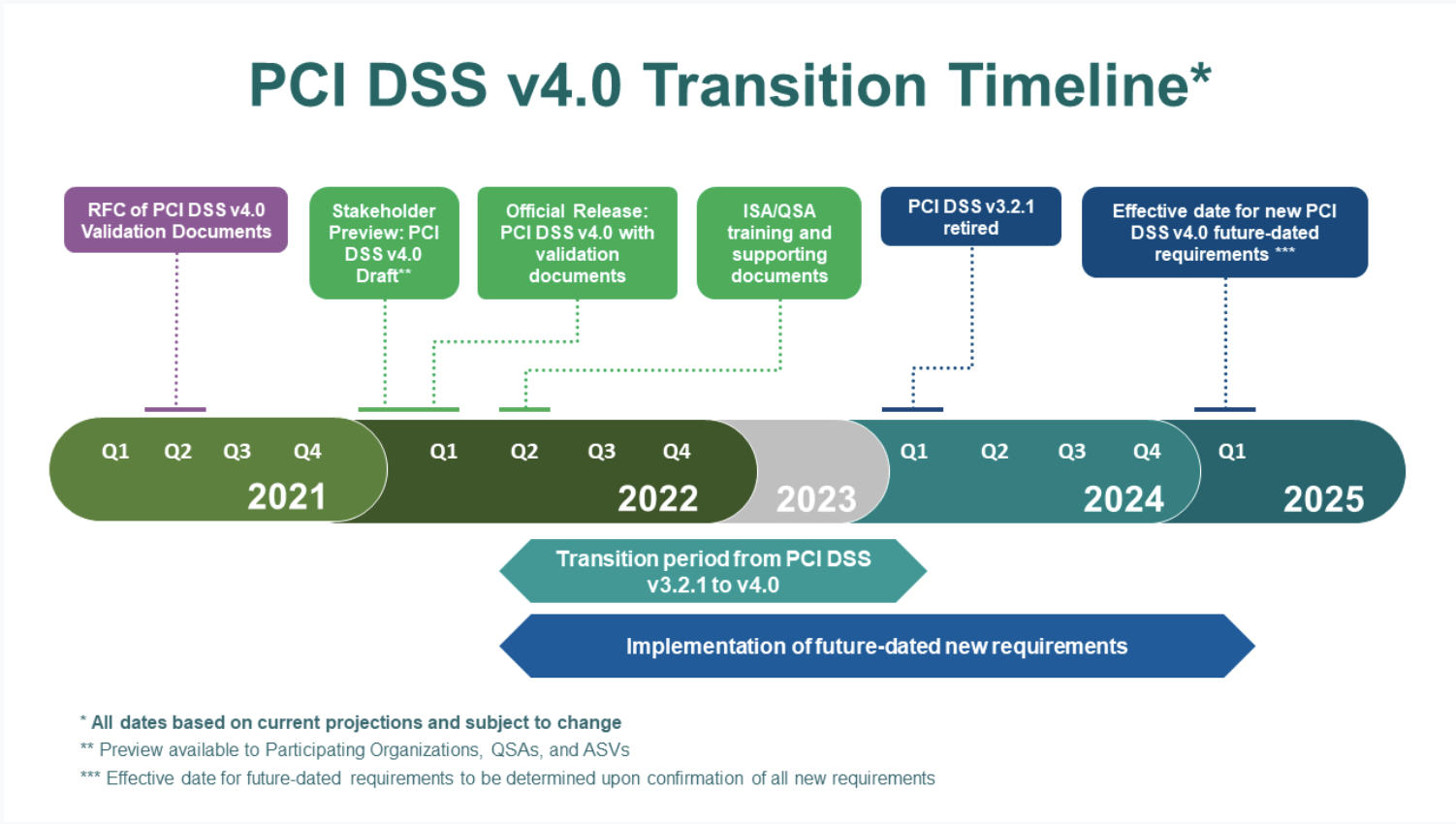
This timeline is crucial, as failure on the part of a credit card processor to comply with PCI-DSS may result in reputation damage and rejection by credit card companies for processing payments. Therefore, it is imperative for companies to implement appropriate security measures to safeguard payment card information well before new compliance requirements go into effect.
Adhering to the new version of PCI-DSS is required for organizations to:
- Protect their customers’ data and their own reputation
- Continue to accept credit card payments
- Avoid fines, losses due to fraud, and loss of insurance
- Demonstrate to other companies, especially merchant banks and card brands, that they are secure and trustworthy.
As a result, the customers of compliant organizations are better protected from fraud, identity theft, personal information leakage, and other malicious activities.
Needless to say, every organization that handles payment card information is taking this update very seriously.
On the Client Side
One of the new requirements for organizations is to keep an inventory of all running scripts, authorize each script (with justifications for why), verify their behavioral integrity, and occasionally conduct risk ranking and vulnerability checks. In addition, there is a new requirement for HTTP header tampering protection for all scripts and resources loaded into the website, which necessitates a system to track the current status and notify of any changes.
The PCI-DSS council recognizes the importance of client-side protection due to the emergence of various attack surfaces in recent years that target the code executed on an end user's device. Supply-chain attacks serve as a prime example of such threats, exploiting the fact that many client-side scripts are loaded from external servers beyond the organization’s control. Common examples of components that are typically hosted on vendor servers instead of organization servers include analytic vendors, ads, and UI/UX components.
Solving the Compliance Problem
When a standard demands specific domain knowledge—such as client-side protection—organizations often choose to use third-party tools to meet their needs.
There are, for example, scanner-based options that periodically scan the website for vulnerabilities. Another option is checks and tests of the static code itself. However, given the security considerations and modern web architecture, relying solely on these methods may not provide the complete picture and could be vulnerable to malicious activities that bypass those check mechanisms easily. A script could be modified and cause significant harm to a business and its reputation between deployment and detection, if the detection process is only carried out weekly or monthly.
In other cases, even if a script is in place just before the scan, it may not run while the scanner performs a check. This is a common occurrence when dealing with web security, as some scripts are specifically designed to identify and evade scanning tools.
Another possible solution is to use tools that rely on real-time traffic. Given the dynamic nature of third-party script updates and their critical role in many organizations, it's essential to have a client-side protection solution that can continuously monitor script behavior, detect any tampering with the script (including headers and all resources), and provide website owners with visibility into the actions of these scripts. By performing detection on the actual website's traffic, a more comprehensive solution can be achieved while ensuring compliance and providing the necessary visibility to website owners.
Using this continuous approach can help strike a balance between development effort, hosting costs, security concerns, and regulatory requirements.
This ensures that the website remains operational while maintaining the necessary security measures to prevent data breaches and leaks. Similar to a WAF, such a tool should enable customers to set policies to enforce and receive notifications of any suspicious activities that do not comply with the policy rules. Additionally, the tool must be capable of reacting in real-time to such suspicious activities—either by mitigating or investigating them—to keep the website protected and functioning properly.
Client-side Defense: The Solution for PCI DSS Compliance
HUMAN Client-side Defense for PCI DSS Compliance offers a robust client-side protection solution that addresses the requirements of the new PCI-DSS version. The solution is designed to meet the new standard requirements, providing script inventory, authorization, and justification; audit trail records; and real-time notification and mitigation of potential risks.
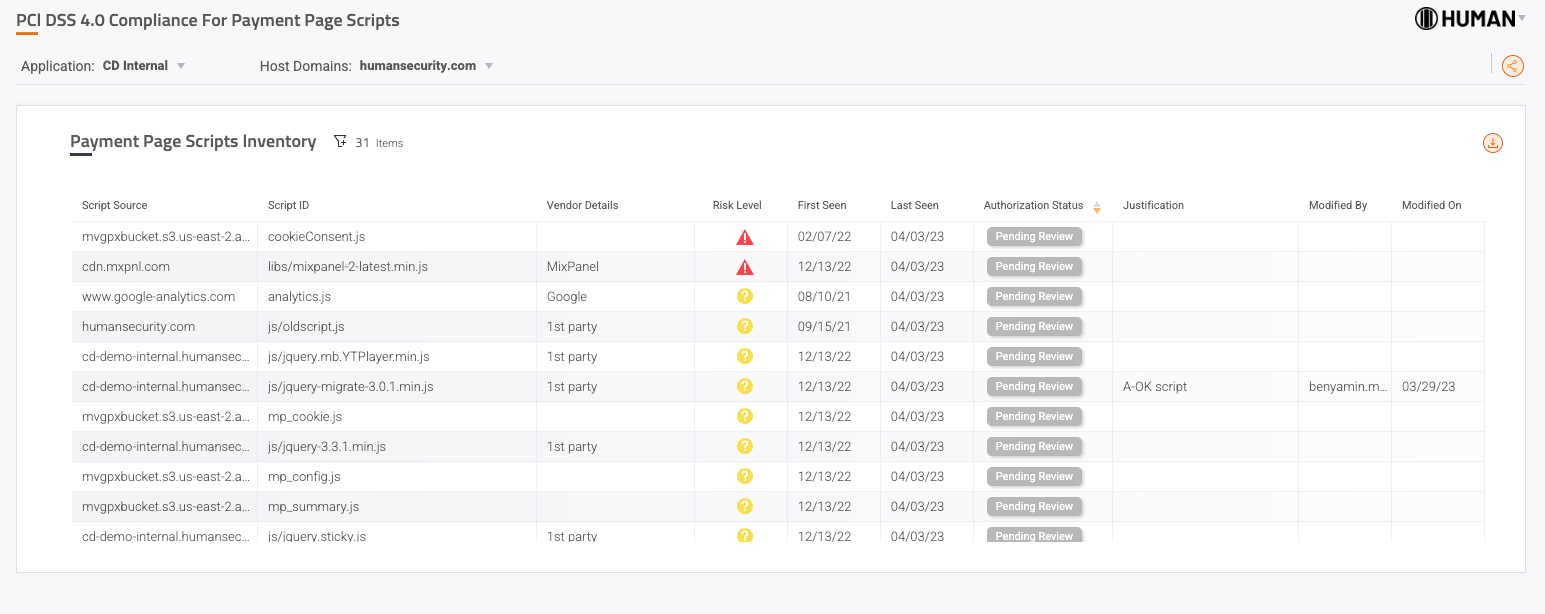
Client-side Defense can establish policies, enforce them, and mitigate any risks in real-time with minimal to no effect on site functionality. It's intelligent detection system is continuously updated to keep pace with emerging threats and vulnerabilities, ensuring that clients are always protected against novel and evolving risks.
Client-side Defense provides customers with comprehensive visibility and control over their website scripts. This empowers organizations to make informed decisions about their website security, with detailed information on script actions, associated risks, script origin, and any new changes and updates introduced into third-party scripts.
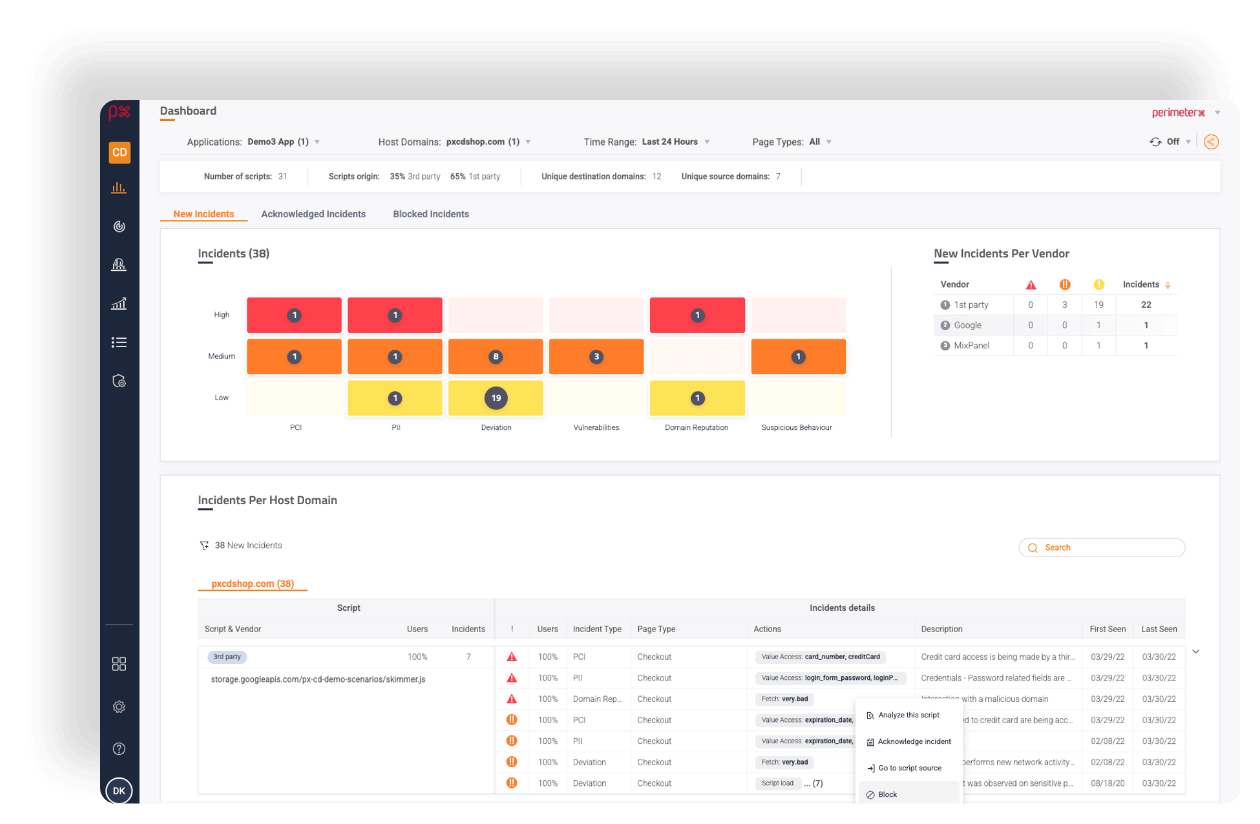
The new PCI-DSS requirements represent a significant shift in the way companies approach payment card data security. Currently, especially when dealing with third-party scripts, client-side applications are the only location where production code runs without control or visibility.
The inclusion of client-side protection solutions means that companies must take a more comprehensive approach to security, considering both server-side and client-side threats. Fortunately, solutions such as Client-side Defense are readily available to assist companies in meeting these new demands and ensuring complete protection of payment card data. Companies that wish to remain proactive in this regard should initiate the integration of such solutions into their websites without delay.